Cybersecurity series: measures to prevent attacks
We continue our series of articles on cybersecurity, this time on key measures to secure your business.
Given that more than 40% of cyberattacks directly exploit the human factor, it is a necessary measure to train employees in cybersecurity, including simulations of attacks on specific people in your company. A cyberattack could have a devastating effect on a society already hit by the coronavirus.
Key measures in the field of cybersecurity
To minimise risks and reduce the likelihood of cyberattacks and data leaks, and to minimise financial impacts in particular, we recommend the following measures:
1. It is true that paper can withstand everything, but cybersecurity should also be underpinned by your formal internal guidelines. At the same time, you should be able to assess the risks and implement measures to mitigate them. In addition, this method will provide you with a suitable tool for ensuring cost-effectiveness.
Formal documentation in the form of internal regulations is the foundation and defines the responsibilities of your users and suppliers. Thanks to it, the framework of their responsibilities and requirements for the company is set.
2. The human factor is one of the most vulnerable elements, so it is necessary to emphasise the regular training of all your users, preferably not only in the form of traditional e-learning, but also ongoing information about new threats. A simulated campaign containing various fake e-mails is also suitable.
a. Most companies use third-party services, such as various cloud solutions, social media, payment gateways, and more. These places usually store your sensitive data or the data of your company. Using the same tools and methods used by today's cybercriminals, our "ethical hackers" can simulate cyberattacks to uncover vulnerabilities in your company.
b. To prevent leaks of sensitive information, regular and thorough training of personnel in cybersecurity is required. Running phishing campaigns on your own employees will provide you with information and statistics that can be used to properly train them and help their further self-development.
3. Regularly test for vulnerabilities in your computer network and perform penetration testing at least once a year.
a. The security test consists of several effective methods of assessing an organisation's resilience to cyberattacks. It will allow you to identify technical, organisational and human vulnerabilities that can pose a risk to your company's reputation and financial and operational capabilities. In addition, security testing helps increase awareness of IT and information security in your organisation.
At BDO, we approach testing as follows:
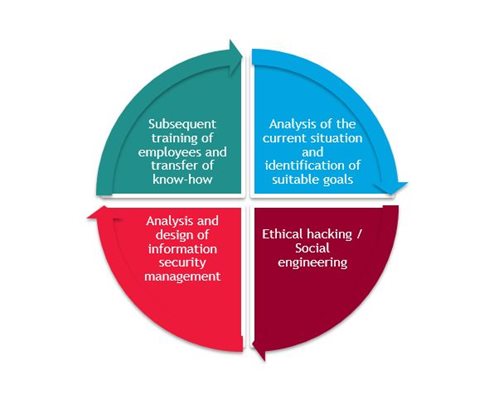
4. Do not use products with discontinued support from the manufacturer, as they pose a great risk.
Products without manufacturer support pose a significant risk to the company. If a new vulnerability is identified, corrective updates are no longer issued for them and they subsequently pose a great risk to the company's computer network.
5. Use only multifactor login for services available from outside the network (internet).
If login is contingent on a second factor (e.g. SMS), protection is provided in case the user's password is leaked. This leakage is risky mainly due to the user's frequent use of the same password in various services, including public ones. Another authentication factor ensures that additional information is required for a successful login.